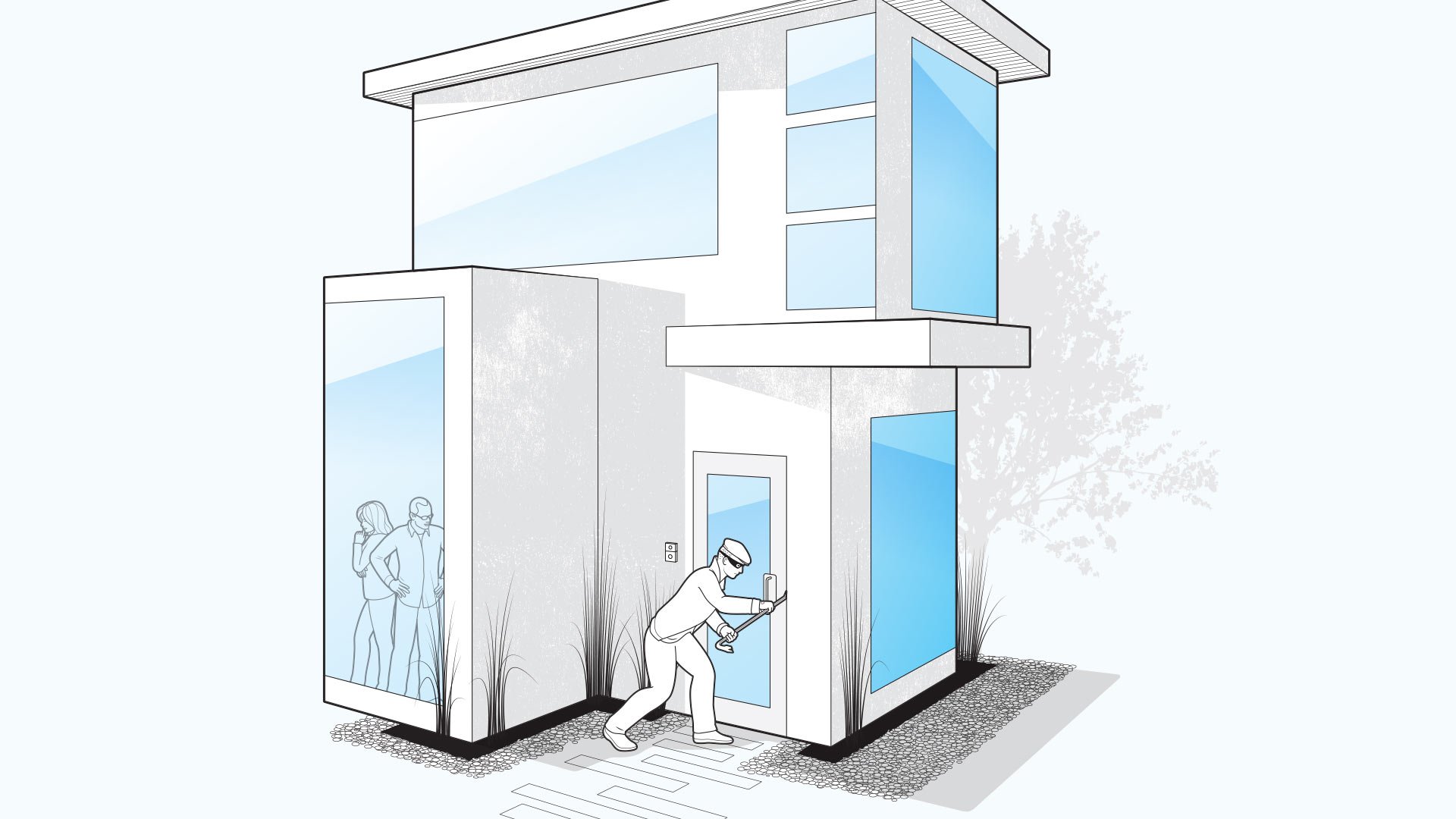
Imagine being at work or on vacation, miles away from your home, when you get a notification on your smartphone telling you that someone is at your door: A motion sensor in the doorbell or someone ringing it can trigger the alert. A homeowner from the Pacific Heights neighborhood in San Francisco got a real-time view of someone stealing his mail in January. He promptly gave the security camera footage, which showed a young man impersonating a Pacific Gas & Electric employee rifling through his mailbox, to a local news station (as well as the police), which soon aired it.
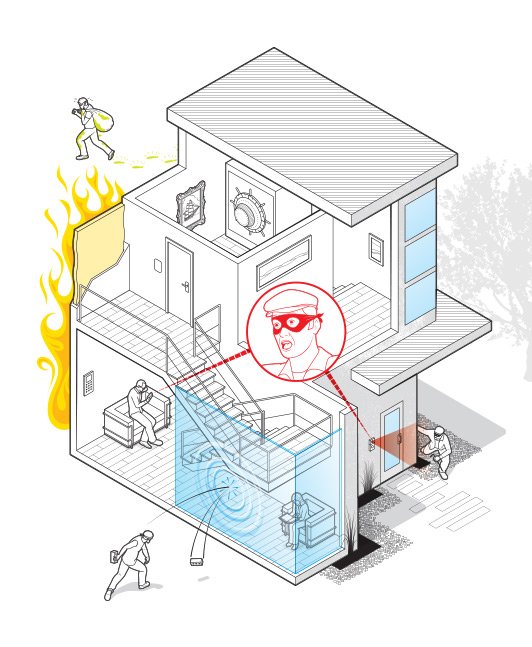
Stories like this one are popping up around the country as technology increasingly takes over the functions of our homes. The most important breakthroughs in home tech not only make your everyday life easier; they also mitigate threats, ranging from house fires to internet phishers. What’s more, they likely increase your home’s value and lower your insurance costs. Here are some of the most significant advances worth considering.

01. CONNECTED DOORBELLS
Having a remote presence
When it comes to keeping your home safe from intruders, one of the simplest systems to install is an internet-connected doorbell. Besides providing video of anyone who comes to the door, connected doorbells let you use your phone to speak through an accompanying intercom, creating the impression that you’re home even when you’re not.
Jamie Siminoff, chief inventor and founder of Ring, the maker of one of the leading connected doorbells—SkyBell is another—says that many people buy one after seeing a neighbor has one. That’s good news for everyone’s safety, he notes. The more connected doorbells a neighborhood has, the more secure the entire area is. (Ring: $199, Jamie Siminoff, [email protected], 917.412.4747, ring.com; SkyBell: $199, 844.256.1826, skybell.com)
02. SMART WINDOWS
Security you can see through
One trend design-minded homeowners appreciate is how new technology can hide the less attractive elements of security. VeriLock windows from custom-window designer Andersen have integrated sensors that tell you not only whether a window is open or closed, but also if it is locked or unlocked. The windows work in partnership with numerous security companies. (Price varies, 651.264.5150, andersenwindows.com)
Bulletproof glass is too thick and unattractive to be a reasonable choice for most homeowners, unless they absolutely require it. But you can strengthen residential windowpanes to slow down intruders significantly, and make them flexible enough to withstand the force of a bomb blast with minimal damage. 3M’s Ultra series of virtually invisible window film resists tearing and keeps shattered glass in place. To install something that can withstand a high-caliber bullet shot at the window, your best bet is to take two plates of tempered glass and then put the 3M film in between them, according to Al Corbi, founder and president of SAFE, a custom security company based in Los Angeles. (Price varies, 888.364.3577, 3M.com)
03. FORTIFIED ENVIRONMENT
Stopping fire at its source
“Your home should be a protective layer so no threat is able to reach you,” says Corbi of SAFE, which has installed security systems for dozens of multimillion-dollar homes, including the $2 billion, 27-story tower in South Mumbai known as Antilia, one of the largest homes in the world.
One of the best protections against a fire, says Corbi, is ceramic insulation, which can be blown into the walls of a home. It doesn’t burn, so it can stop a fire from traveling, and it also protects you from the heat of a fire. Since heat and smoke are the biggest dangers in a fire, installing specialized air filters helps clean the air coming into a room, while a pump forces contaminated air out. The whole system costs only a few thousand dollars and has the added bonus of being able to purify the air against allergens and other contaminants. (Price varies, Lana Corbi, executive vice president, [email protected], 202.484.9500, safe-us.com)

04. THEFT DETERENTS
New ways to thwart intruders
If a traditional camera or radar setup isn’t proactive enough for you, technology offers plenty of ways to booby-trap the perimeter of your home against would-be invaders. Heracles Research, a Frisco, Texas-based company, offers a variety of devices that deploy pepper spray and set off an alarm if a trip wire is activated. (Price varies, [email protected], 214.618.1368, burglarblaster.com)
Several companies make it possible to mark thieves by spraying them with dyes that fluoresce under UV light. British companies such as SmartWater (not the beverage brand) and SelectaDNA offer consumers and businesses sprays that are linked to an address or a person, so if a thief is caught with that solution on their hands or clothing, they can be linked back to a specific crime. These sprays can be used to identify your stolen property if it was marked as well. (SmartWater, 44.870.242.8899, smartwater.com; SelectaDNA, [email protected], 865.935.8518, selectadna.com)
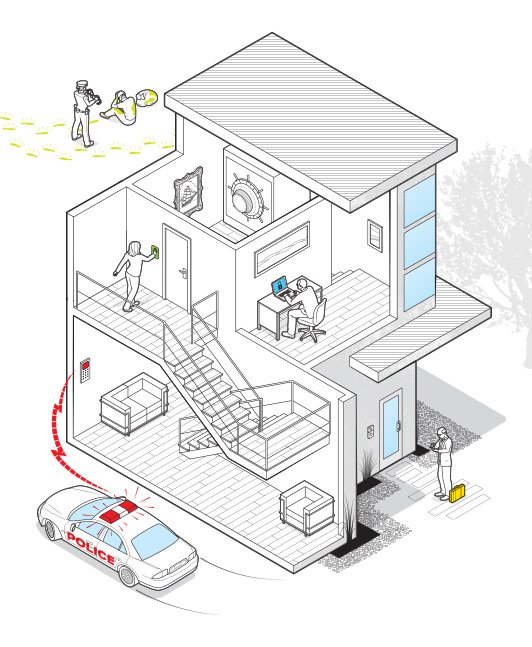
05. INTELLIGENT ALARM SYSTEMS
Combining home forces
A traditional alarm system will mitigate security risks to your home, but a blend of home automation and security will go quite a bit further. Security firm ADT’s version of this combines its traditional security sensors with lighting and new smart home devices such as the Nest thermostat. “Before, we were putting in a fire alarm system and we were done,” says Tim McKinney, vice president of ADT Custom Home Services. “Now, when we’re working with the lighting and automation systems, we can light the way and unlock the doors at the same time we shut down the HVAC once the system actuates. All these things are happening simultaneously.” (Price varies, 800.521.0772, adt.com)
A key component of any alarm system is a duress code that can be entered into the keypad in case a home invader forces you to disarm the alarm. The code will appear to shut off the system but trigger a silent alert for help. Most systems come with a default duress code, but many homeowners don’t realize they have this potentially life-saving feature.
06. BIOMETRIC SECURITY
Beyond fingerprints
Controlling access to a home or a room housing a valuable collection could be as simple as installing a biometric device, but leaders in the field are moving beyond fingerprint recognition. Fingerprint readers can be temperamental things with a failure rate of 10 to 15 percent, according to various studies. Palm readers, in particular, are becoming a go-to way to ensure only authorized visitors enter. Why a palm reader? Industry experts say that the blood vessels in the palm are as unique as a fingerprint and more easily scanned.
07. DIGITAL SAFETY
Stopping Cyber Attacks
Even if you think your home is secure, there are usually still weak links. Greg Conti, associate professor and director of the Army Cyber Institute at West Point, spends much of his time thinking about those vulnerabilities. “There is no panacea and no completely safe technology,” he says. “There are things you can do with the technologies to make yourself safer once you understand what you are trying to protect and what you are trying to protect it from.”
Intruders don’t have to be physically present to break into your house. A hacker might try to get access to a WiFi network to compromise security systems or take control of internet-enabled devices. Since everything from refrigerators and toasters to televisions, lighting and even children’s toys is connected to your network, a determined hacker could commandeer those devices to spy on you, acquire information to use against you or harass and threaten you.
Because your network holds the virtual key to your home, make sure you use encryption to secure it. Limit access to it and establish a strong password. Before buying extra gear or new network services, it’s worth checking your passwords and educating your family about common security risks. For example, most people know that “password” is the least secure password, yet an annual survey by Los Gatos, Calif., security firm SplashData that looked at more than 2 million leaked passwords available online in 2015 found that, for the fifth year in a row, “password” was the second most common password. (The most common was 123456.)
Digital criminals also send phishing emails to try to steal your identity or install malicious software that might give them access to your banking passwords. Conti, who keeps a piece of black tape over the webcams on his computers to prevent spying, suggests the purchase of a $200 Chromebook computer, which has many security features such as local data encryption and the inability to install malware (or any software). Use this separate machine for doing any online banking and secure transactions—and only those transactions. Don’t use it to surf the internet or check your email.
08. THE FINAL STEP
Checking for vulnerabilities
Once your passwords are set, your gear is all updated, your networks are in place and your digital perimeter is secure, it’s time to test it. According to Michael Belton, vice president of applied research at Denver-based cybersecurity firm Optiv Security, you can hire a company to do penetration testing on your home network. This would include three days or so of attempts to crack your WiFi network and tests to get into your devices. When those are done, you get a report that lets you know what to fix and how much it will cost to do so. (About $10,000, Michael Belton, 303.298.0600, optiv.com)
All of these measures contribute to the security of your home and data, but bear in mind that security is an arms race, and the bad guys spend more time thinking about it than you do. As Belton points out, even Bill Gates and John Brennan, the director of the CIA, have been hacked. And of course, the greater your wealth or visibility, the more likely you are to be a target—the risks become more subtle, the invasions more ambitious. Some thieves might go so far as to bribe contractors or repairmen to install eavesdropping devices. To protect against that threat level, you really need a dedicated security specialist.
For more information on advances in home security and what to look for in a security consultant, visit worth.com.